The Onion Router Project is one of the best inventions today’s netizens can ask for. Better known by its acronym Tor, it offers conditional but free anonymizing solution for millions of internet users across the world. Tor relays internet traffic over the volunteer relay network to offer better privacy and security to internet users. The main objective of Tor is to help users overcome surveillance and monitoring of internet connections and activities by governments and other entities.
Tor allows users to create proxy connections that helps overcome internet censorship. The open source software is used by individuals, activist groups and developers alike to suit their needs. Majority of bitcoin community also prefers to use Tor during transactions to ensure privacy. It is also necessary to access the deep web. However, like any other software, Tor also has room for constant improvement and the open source community regularly contributes to make it more safe and secure for users.
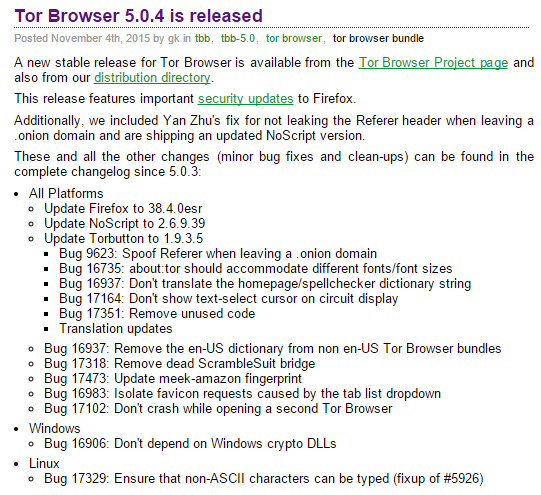
Recently Tor released the latest update — version 5.0.4. The new stable release of Tor browser package is reported to contain various fixes and security updates including the ones recommended for the Mozilla Firefox ESR which it uses as the browser client. Most of the security fixes are listed on Tor Project’s official blogpost.
Tor Update Strengthens Security and Privacy
One of the most important fix among all is the Yan Zhu fix, named after the person who developed it. It prevents leakage of HTTP Referrer header when the user navigates from a .onion domain to a normal one. Referrer header may pose a potential risk to privacy as it may contain information that can potentially compromise the user’s identity, location, browsing history etc.
In addition to Yan Zhu fix, the Tor community has also addressed bugs that affected Windows and Linux systems. The Windows bug fix labelled 16906 removes the dependency on Windows’ default module that handles Certificate and Cryptographic Messaging functions in CryptoAPI (Ref- MSDN library). The bug fix allows Tor to function without making use of the mentioned Crypt32.dll and Wintrust.dll, reducing the Tor browser’s dependency on Microsoft APIs to operate. Before the fix, the Firefox browser was dependent on these files for operation and any errors could crash the browser. It also prevents unauthorized digital signatures from IP spoofing and gaining/transmitting device information to the network.
The Windows bug 16906 fix on latest Tor browser package update takes no chances, avoiding potential breaches in privacy. The Linux Bug 17329 fix offers a better browsing experience for users on Linux PCs by enabling non-ASCII characters.
With the latest update, bitcoin users can confidently conduct transactions over the Tor network without worrying about their anonymity being compromised. Their activity on updated Tor browser is as isolated as it can get from the possible identifiers associated with their computer’s operating system.
Reference:
Tighter Control Over Your Referrers - Mozilla Security Blog
Microsoft Dev Center - Crypt32.dll
























Tor is not safe. Government developed Tor for the Navy, therefore they are the creators, they can monitor everything you do on Tor. I would suggest using Hide My IP VPN for accessing Deep Web, to ensure your safety and privacy…